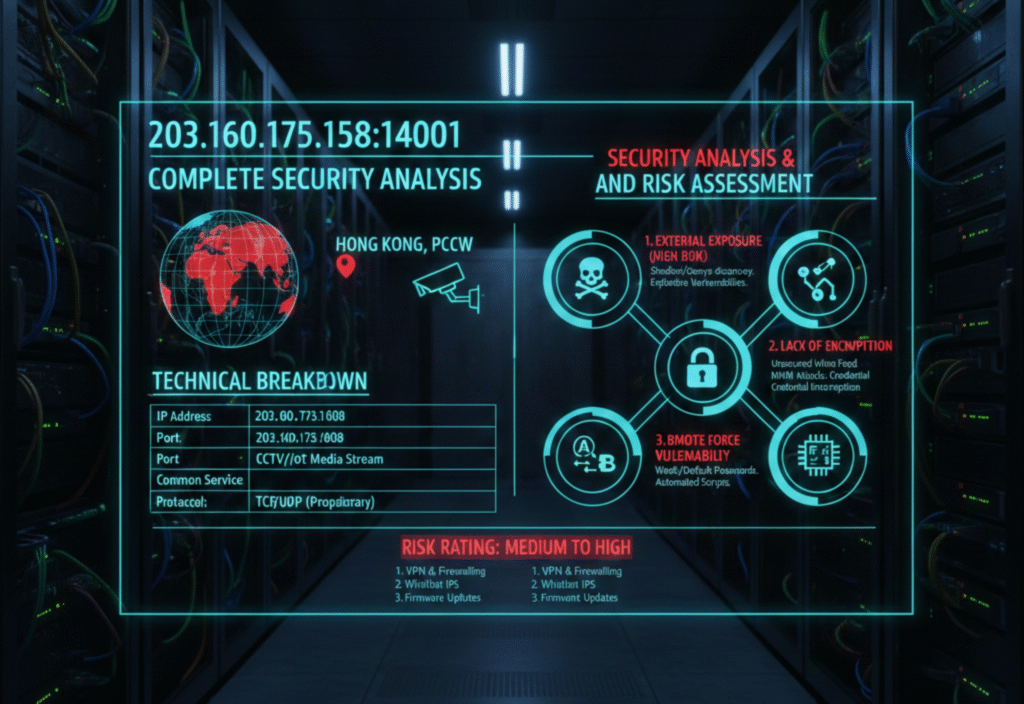
When you see an address like 203.160.175.158:14001, it may look confusing at first. However, this combination is simply a reference to an IP address and a specific port on a server. Together, they help devices on the internet communicate with a particular service.
Understanding what an IP address and port number represent is useful for network learning, cybersecurity awareness, and safe online practices. In this article, we will break down the meaning of 203.160.175.158:14001, explore how it works, and provide a complete security analysis and risk assessment.
What Is an IP Address and Port Number?
An IP address like 203.160.175.158 is a numerical label assigned to a device connected to a network. It acts like a digital street address, so data knows where to go.
A port number such as 14001 tells the network which specific service or application on that device should receive the data. Think of the IP as the building and the port number as the room number where a particular service is located.
Together, 203.160.175.158:14001 is a unique access point that can direct traffic to a particular service or application hosted on a server.
How 203.160.175.158:14001 Works
This combination works as an endpoint that devices and applications can use to communicate over the Internet. Specifically:
203.160.175.158 identifies the host or server.
14001 tells the system which application or service on that host should be contacted.
By specifying a port, servers can run multiple applications at once without conflict. This allows for efficient use of resources and clearer routing of network traffic.
Common Uses of 203.160.175.158:14001
Addresses like this may be used in several ways:
1. Web or API Services
Some online services are hosted on non‑standard ports like 14001 for specialized access. This might include internal dashboards or web interfaces.
2. Remote Management Tools
Administrators sometimes use unique ports to access control panels or management interfaces remotely.
3. Application Testing
Developers and testers may use such endpoints in development environments to test applications before wider deployment.
4. Database or Custom Software Connections
Custom applications often use specific ports to separate traffic and avoid conflicts with default services.
Security Risks to Be Aware Of
While using an IP address and port for legitimate purposes is normal, there are security considerations to keep in mind:
Open Ports Can Be Targeted
Open ports can become entry points for unwanted access if not protected properly. Hackers often scan for open ports to find vulnerabilities.
Unauthorized Access
If proper authentication is not enforced on services at 203.160.175.158:14001, attackers might try to connect and misuse the service.
Firewall and Network Protection
Without firewalls or access controls, services running on a port can become easily reachable by unauthorized users. Monitoring and restricting access is essential.
Monitoring and Threat Detection
Using security monitoring tools can help alert administrators if someone repeatedly tries to access a port without permission.
Important: There is no public evidence that 203.160.175.158:14001 is intrinsically malicious. However, any exposed IP and port on the internet should be treated with care if you do not control it. Always verify ownership before connecting to an endpoint.
Best Practices for Safe Use
Here are practical recommendations for handling IPs and ports securely:
1. Confirm Ownership
Only access such endpoints if you know they belong to your organization or a trusted service.
2. Use Secure Networks
Access endpoints over secure connections like VPN, especially when using non‑standard ports.
3. Enable Authentication
Make sure any service accessible via a port requires strong authentication and encryption.
4. Regular Updates
Keep the server and applications updated to prevent exploitation of known vulnerabilities.
5. Firewall Rules
Configure firewalls to allow only trusted IPs and restrict access where necessary.
Troubleshooting Connection Issues
Sometimes connections via a specific port might fail. Common reasons include:
Port blocked by a firewall
Service not running on the port
ISP restrictions
Misconfigured network settings
Using tools such as network diagnostics can help identify and fix these kinds of issues.
Conclusion
In summary, 203.160.175.158:14001 is a combination of an IP address and a specific port that indicates a particular service on a device or server. It plays a standard technical role in networking and can be used for web services, remote management, testing, or custom applications.
However, accessing any such endpoint should always be done carefully and responsibly. Proper security configuration, authentication, and monitoring help reduce risk and keep systems safe.